
janet nduku

janet nduku
Share:
Related Posts

ZKTeco East Africa is heading to INTERSEC Dubai 2026!
INTERSEC Dubai 2026! ZKTeco East Africa invites partners, clients, and industry stakeholders to schedule a meeting with our team. This session provides an opportunity to

Introducing Our Superior Solution for Current Market Needs – The Z8636NMR-S ZKBio Sense Smart NVR
We are proud to introduce the Z8636NMR-S ZKBio Sense Smart Network Video Recorder, a cutting-edge solution engineered to directly address the most pressing needs of

Best Time and Access Control Solution for Businesses: Experience BioTimeCloud with a 90-Day FREE Trial
Managing employee attendance across different branches, worksites, or field locations has always been a challenge for growing businesses. Manual processes often lead to errors, inconsistencies,
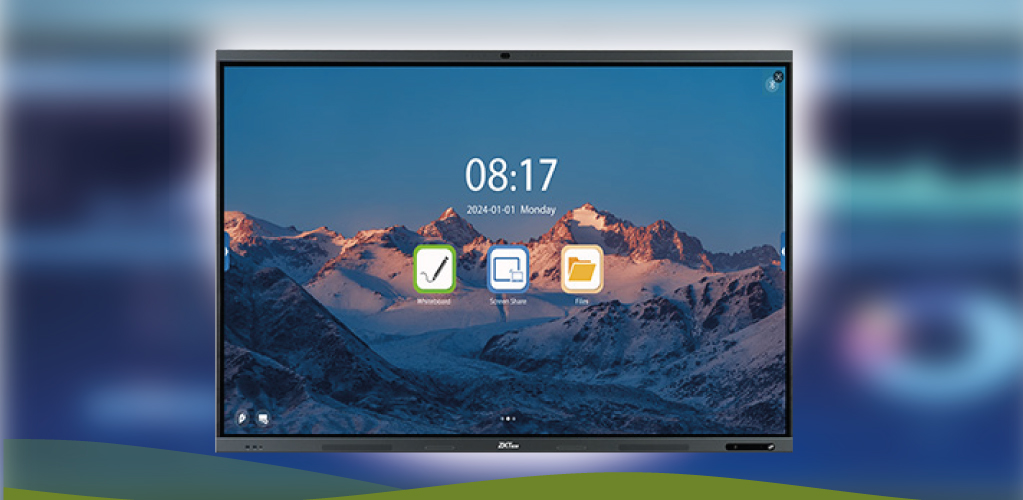
Interactive Smart Board: Revolutionizing Modern Learning and Collaboration
The Future of Interactive Display Technology Interactive Smart Boards have transformed the landscape of modern education and business collaboration, replacing traditional whiteboards with sophisticated digital

Join the “ZKTeco Hunt Challenge” on TikTok!
In celebration of our TikTok debut, unleash your creativity by showcasing ZKTeco products in captivating videos. Simply upload your creation on TikTok, tag ZKTeco’s official accounts,
Share:
Leave a Reply Cancel reply
Related Posts

ZKTeco East Africa is heading to INTERSEC Dubai 2026!
INTERSEC Dubai 2026! ZKTeco East Africa invites partners, clients, and industry stakeholders to schedule a meeting with our team. This session provides an opportunity to

Introducing Our Superior Solution for Current Market Needs – The Z8636NMR-S ZKBio Sense Smart NVR
We are proud to introduce the Z8636NMR-S ZKBio Sense Smart Network Video Recorder, a cutting-edge solution engineered to directly address the most pressing needs of

Best Time and Access Control Solution for Businesses: Experience BioTimeCloud with a 90-Day FREE Trial
Managing employee attendance across different branches, worksites, or field locations has always been a challenge for growing businesses. Manual processes often lead to errors, inconsistencies,

Interactive Smart Board: Revolutionizing Modern Learning and Collaboration
The Future of Interactive Display Technology Interactive Smart Boards have transformed the landscape of modern education and business collaboration, replacing traditional whiteboards with sophisticated digital

Join the “ZKTeco Hunt Challenge” on TikTok!
In celebration of our TikTok debut, unleash your creativity by showcasing ZKTeco products in captivating videos. Simply upload your creation on TikTok, tag ZKTeco’s official accounts,
